Thanks mechbgon ...
Use a layered defense.
Layered defense means that you don't rely on just one type of defense (such as antivirus software). Instead, you use multiple overlapping layers of defense. Some of the most powerful layers of defense are already built into Windows (or even built into your hardware!). You don't need to download them, buy them, or even install them... you just need to start using them.
Bye-bye, Windows XP You can adapt most of this info to WinXP, but I'm now writing this page on the assumption you've got Windows Vista or Windows 7. Both of them are far more practical to run securely than WinXP was.
Shortcuts to the suggested layers (or just scroll down the page)
- Use non-Administrator user accounts
- Use a firewall and a router
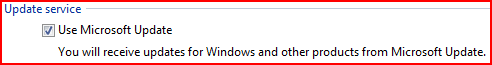
- Enable Automatic Updates and upgrade to the Microsoft Update engine
- Uninstall software you don't use
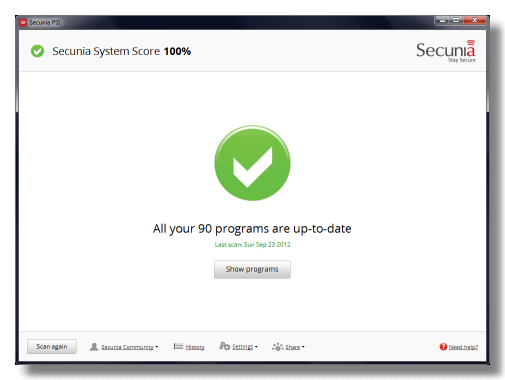
- Use Secunia's checkup to fix vulnerable software
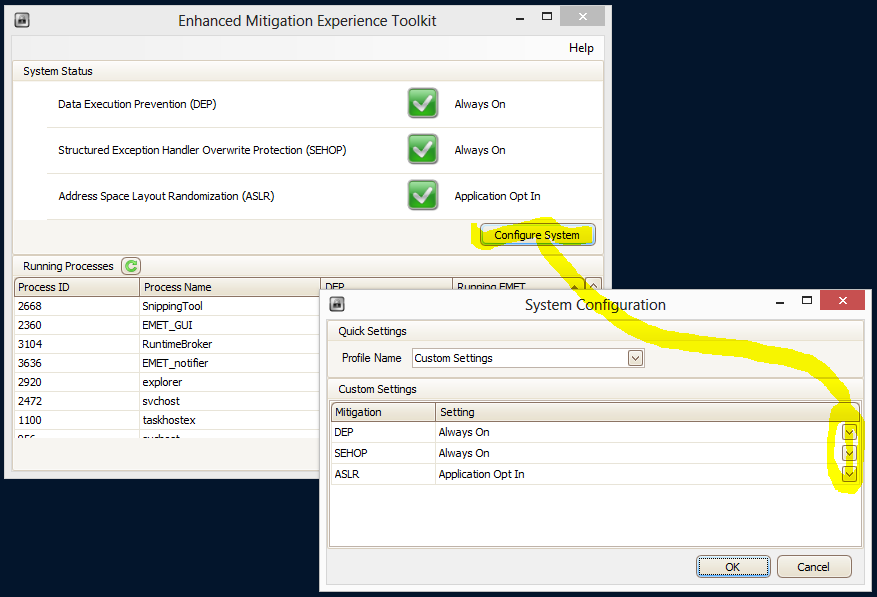
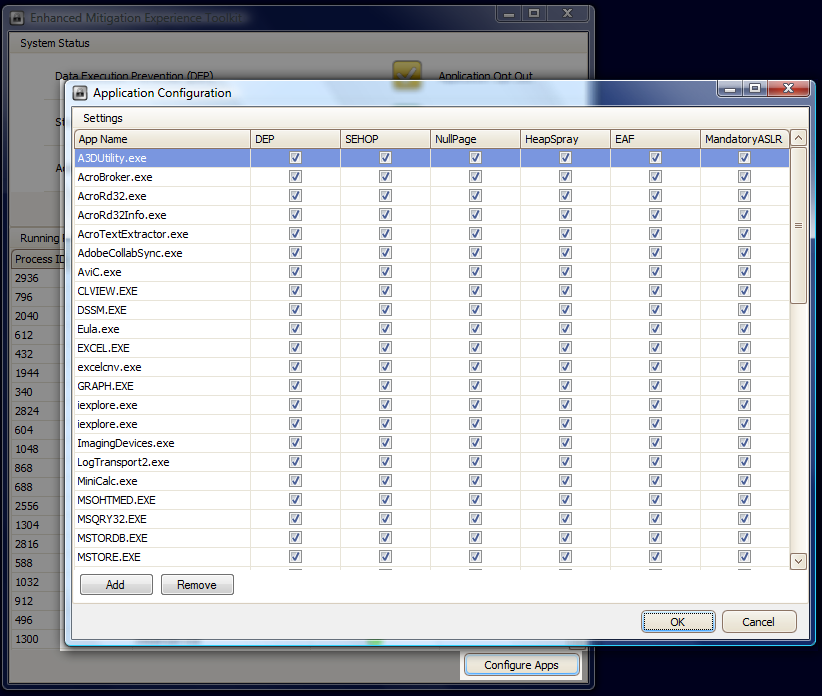
- NEW! Use the free Microsoft EMET security enhancement kit
- Win7 and Vista users: update Internet Explorer to version 9
- Win7 and Vista users: keep UAC enabled
- Use antivirus software
- Disable or restrict AutoPlay
- Recognize trojan-horse programs
- Recognize phishing scams
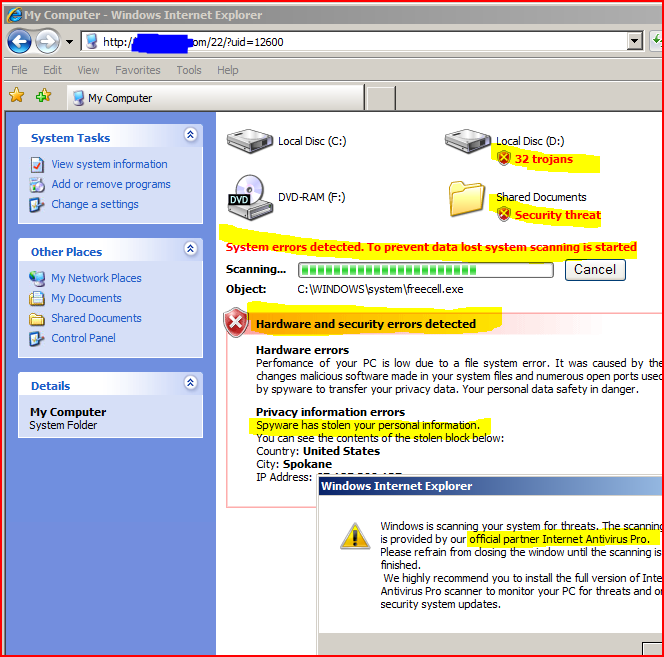
- Recognize scareware scams
- Back up your important data
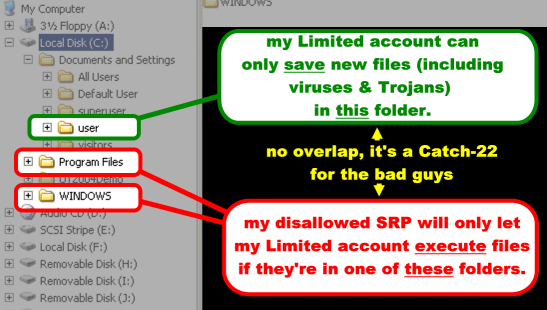
- Advanced users: try Software Restriction Policy or Parental Controls
Is all this proactive computer security that important? Yes. For example, if the bad guys infect your computer and steal your bank log-in credentials, they can empty your bank account and ruin your credit rating. Or they can do the same thing in your virtual life, stealing your World Of Warcraft stuff. Deleting the malware that stole your credentials won't undo the damage, so don't wait for the bad guys to make the first move. This stuff's happening right now. Get your computer hardened up.
Suggested defense strategy for home computers
|
|
|
Browser security: what about alternate Web browsers?
Use an alternate browser instead of Internet Explorer if you prefer, but don't make it your answer to security. All web browsers, and their add-ons and plug-ins, will always have exploitable security vulnerabilities. The first step in browser security is not to trade one set of browser vulnerabilities for another set, but rather to put ALL of them into a cage, by depriving the browser of Administrator-level privileges at a minimum. The second step to browser security is still not to trade one set of browser vulnerabilities for another set... it's to make sure your browser add-ons / plug-ins are up-to-date. A perfectly-secure browser can still be used to exploit a vulnerable version of Java, Flash Player, QuickTime Player, etc. Browser extensions are the big "attack surface" today, not the browser itself. This was brilliantly demonstrated by Flash-driven "clipboard hijacking" attacks in 2008 that worked on Linux, Mac and Windows, regardless of the web browser. And for the third time, uninstall Sun Java completely unless you really need it for something, it's a real exploit magnet. On Windows Vista and Windows 7, I'd stick with Internet Explorer 9. Protected Mode, best-in-class detection rates on malicious sites, Tracking Protection options, centrally manageable and enforcable... it's pretty solid, this isn't your father's Oldsmobile ;) Use EMET to make it even tougher.  Internet Explorer runs in Protected Mode by default on Windows Vista and Windows 7. For more information on Protected Mode, try this moderately-technical TechNet article. 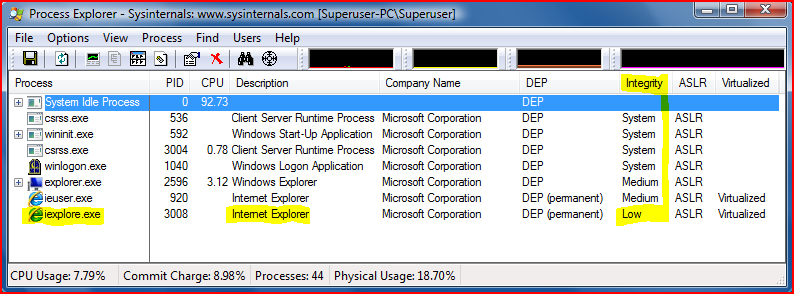 Windows Vista and Windows 7 run Internet Explorer at the lowest Integrity level available, as an additional proactive damage-containment countermeasure. If you're interested in Windows Integrity Control, see this 2-page article at SecurityFocus. In addition to selectively disabling Javascript / active scripting as shown in the video, you can also use the Zones to selectively disable ActiveX and Java applets (Java is different than Javascript). If you have Internet Explorer 7 or 8, ActiveX is already disabled for all ActiveX controls except the ones you've "opted in" yourself. more information on ActiveX opt-in Remember that legitimate mainstream websites are routinely hacked, so don't assume that these techniques protect you from all scripted attacks. But whether you prefer Internet Explorer or some other browser, restricting Javascript, Java applets and ActiveX controls to just a whitelist of trusted sites is certainly a security enhancement, if you can live with the maintenance of it. |
|
Why don't you don't list any antispyware programs? Every other security guide seems to list three or four! If you use the layered defense I've shown above, starting with a non-Administrator user account, then it's extremely unlikely that you'd need antispyware programs. If you want to install some anyway, here are some reputable free ones. Do note that the techniques used to "immunize" web browsers can cause them to be slower.
Get a Tracking Protection List Internet Explorer 9 lets you add a Tracking Protection List. In IE9, click the gear symbol at the upper-right, choose Internet Options, and click the Manage Add-Ons button on the Programs tab. Click on Tracking Protection and you'll see what to do from there. |
|
I heard the Windows Firewall isn't very good For the purpose
of keeping other computers (even those sharing your router) from
attacking your own computer, it's fine. Windows won't let your
non-Administrator account (or something exploiting your non-Administrator account) mess with the Windows Firewall settings either, making it especially tamper-resistant. Some people want a "two-way" firewall that'll ask them before letting a program use the Internet connection, but these historically have been easy to fool, so I wouldn't place too much confidence in that capability. I use the Windows Firewall and simply maintain tight control of what's on the computer in the first place. |
|
OK, I admit it... I browse risky websites. Any tips? In addition to the other steps listed above, create a separate non-Administrator user account just for high-risk usage. Edit the file-system security on your storage drives so this account doesn't
have access to them. If something does get control of the account, it
won't be able to get at your important files to delete them, encrypt
them to hold for ransom, or steal copies of them. When I hunt malware
in the wild, I do so from a separate non-Administrator account named
"Malware Research." Again, if you have Windows Vista or Windows 7, this
is a great use for Internet Explorer in Protected Mode (which is the
default setting). |
| Anything else? Since this is a guide to building a new computer, I strongly suggest getting a 64-bit version of Windows, preferably Windows 7. My personal pick would be Windows 7 Professional Edition, because it has Shadow Copy, better Backup features, and is capable of Software Restriction Policy. See the previous page for more information on Windows variants. |

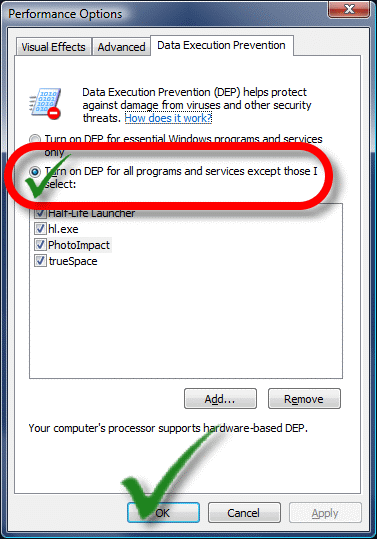
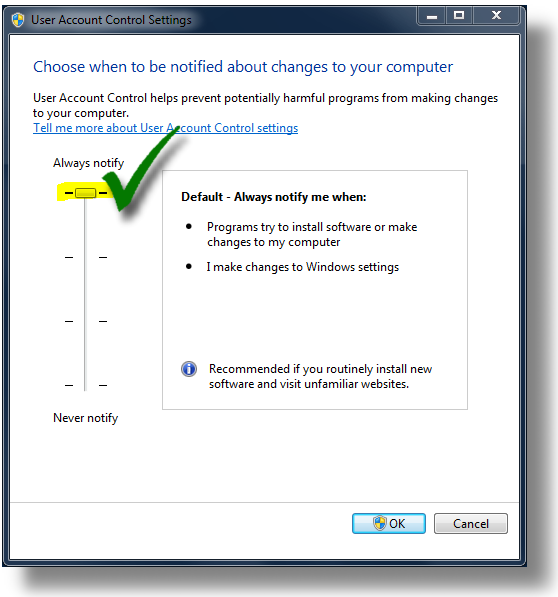
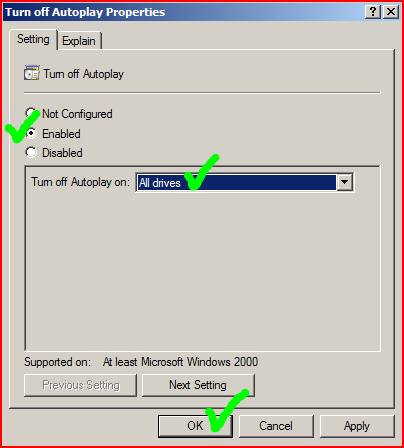
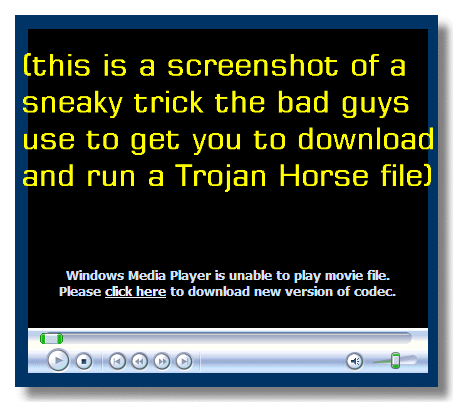
 :a
:a
 :b
:b
 :c
:c
 :d
:d
 :e
:e
 :f
:f
 :g
:g
 :h
:h
 :i
:i
 :j
:j
 :k
:k
 :l
:l
 :m
:m
 :n
:n
Tidak ada komentar:
Posting Komentar